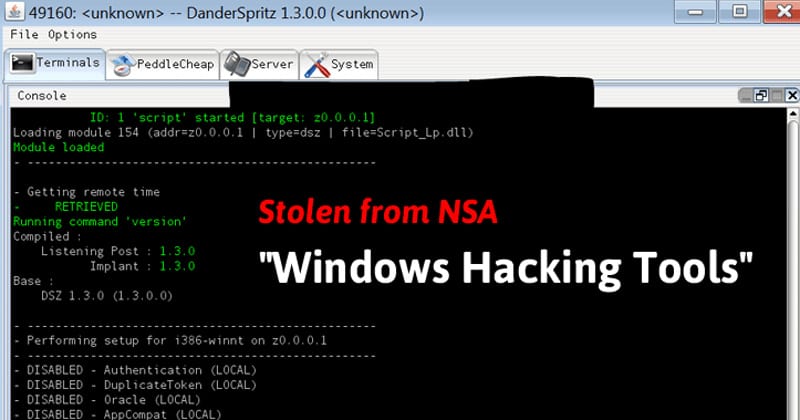
Now it looks like security researcher Sean Dillon from RiskSense said that he ported three exploits EnternalChampion, EternalRomance, and EternalSynergy that were stolen from NSA last year. According to the reports from BetaNews, Sean Dillon managed to modify the exploits to target two different vulnerabilities that exist in most of the Microsoft’s Windows operating system. The security researcher has merged the exploits into open-source penetration testing project the Metasploit framework. The researcher found that these exploits can impact even the newest operating system like Windows 10. Well, Windows 10 is believed to be safe to flaws stolen from the NSA last year, but, the new research shows a different story. EternalSynergy can take advantage of both CVE-2017-0143 and CVE-2017-0146 vulnerability, EternalRomance is only targeted at the first, while EternalChampion targets the latter. The researcher has published the documentation on Github in which it explained that the Windows version released between 2000 and 2016 are vulnerable and an attacker can obtain admin rights on a compromised host. Sean Dillon said “You can run any command as SYSTEM, or stage Meterpreter. Note: unlike EternalBlue, kernel shellcode is not used to stage Meterpreter, so you might have to evade your payloads” Well, it’s worth to note that these new exploits can only compromise an unpatched Windows operating system, so it’s critical for Windows users to install the latest security updates as soon as possible. So, what do you think about this? Share your views in the comment box below.
Δ